If you’re reading this, there’s a 50/50 chance you’ve been hit by ransomware this year already, according to an Osterman Research Study.
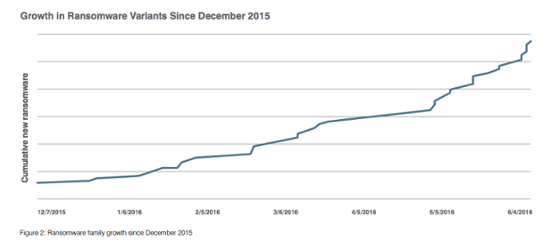
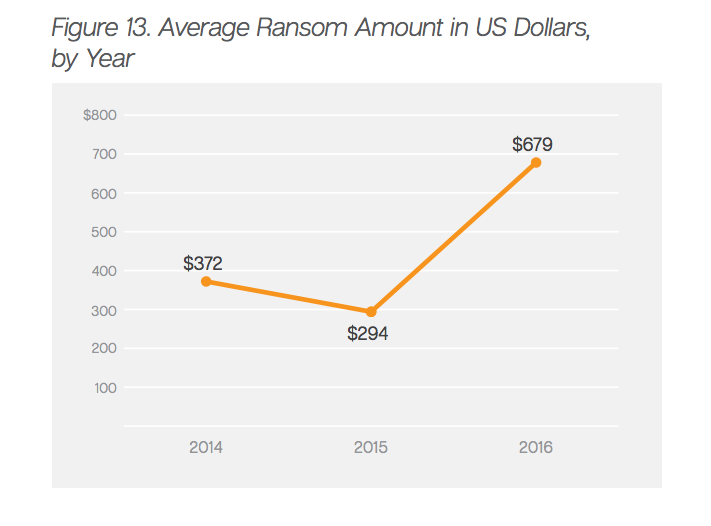
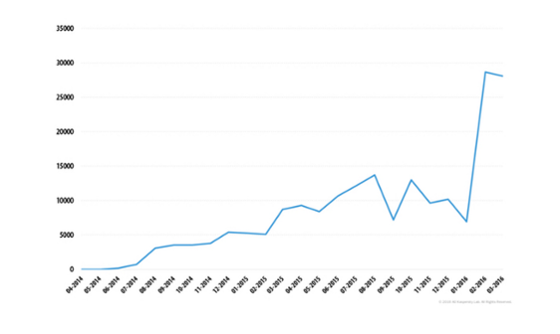
Since last year, ransomware attacks have more than doubled, jumping from 23k to a staggering 56k. And to make matters worse, the average ransom has skyrocketed from $294 to $679.
Translation? Malware is hitting twice as often and twice as hard.
For the full brief on the 2016 malware menace, read our rundown. And remember, the only sure-fire way to protect your data from ransomware is a strong backup strategy!
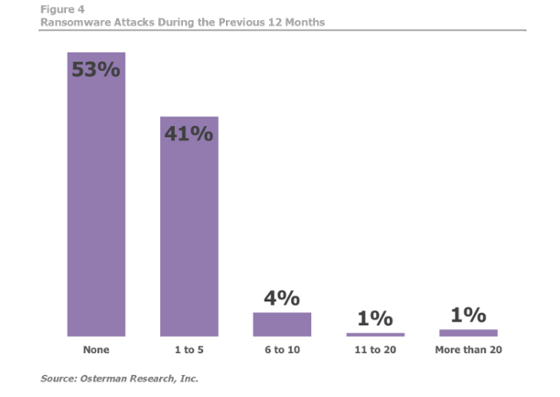
Study: Almost Half of Businesses Have Been Hit By Ransomware in 2016
…And if you’re part of the particularly unlucky six percent, you’ve been hit up from ransom money at least six times, if not more. The fact that one percent of businesses have been hit more than 20 times by ransomware is staggering. And only four percent of U.S. respondents said they were confident in their current security’s ability to prevent future attacks.
Ransomware-As-A-Service (RaaS) Is Paying Out
In the first quarter of 2016, the FBI reported $209 million was paid out to ransomware criminals. Now that Ransomware is being offered as a service, anyone can use it regardless of their technical knowledge. This goes a long way to explain the sudden spikes.
It’s also believed the doubling of the average ransom amount is due to the success of several high-profile, high demand attacks. Even though the average demand is now $697, the success of the $17,000 ransomware attack on the Hollywood Presbyterian Medical Center in February shows criminals often ask for more. And what’s worse, they’re getting away with it.
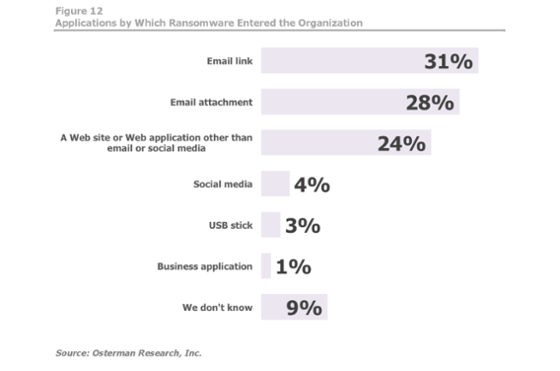
Email Is Still the #1 Delivery Method for Ransomware
Monitor those inboxes – Emails still make up 59% of all ransomware infections. Which means that not only is good backup practice important, users should be thoroughly trained in anti-phishing techniques to minimize this threat.
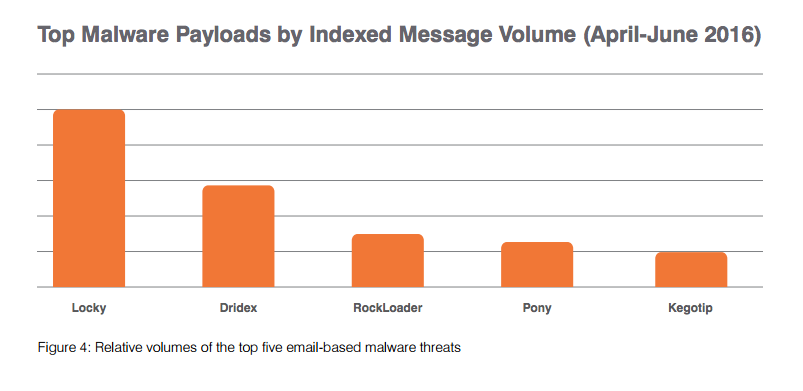
Locky: The Current King of Ransomware
If you opened an email and got infected by ransomware in 2016, chances are it was Locky. This malware hides itself in MS Word documents and executes by macros. It is almost exclusively distributed by spam e-mail campaigns powered by the Necurs botnet, which also distributes its nearest competitor, Dridex.
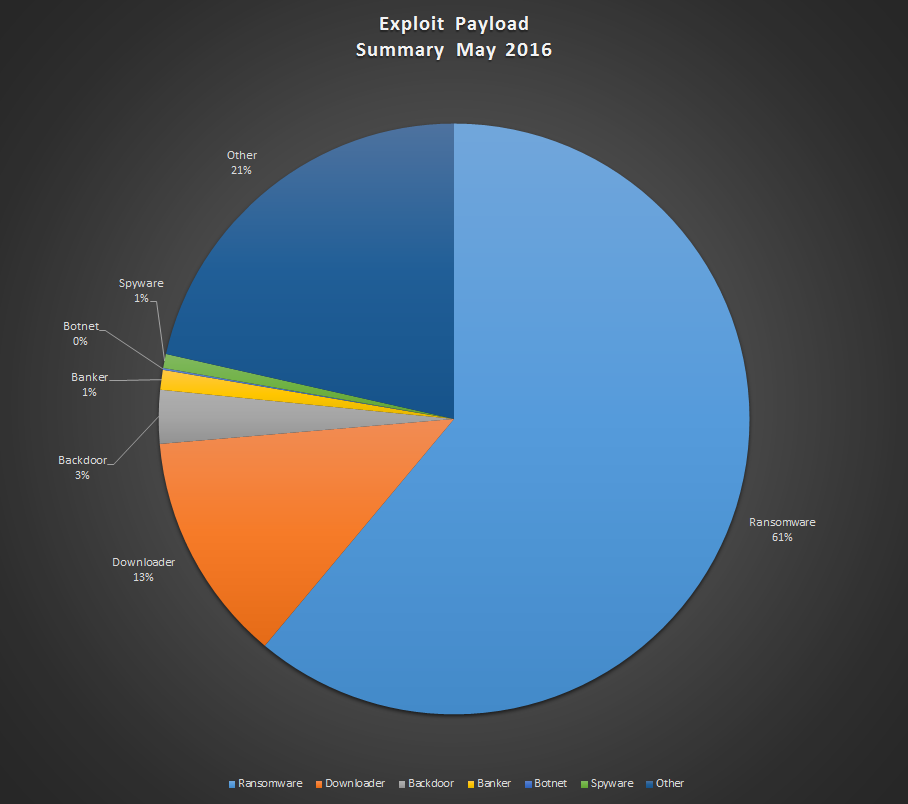
Exploit Kits Are on the Rise
Email might be dominating the ransomware industry now, but exploit kits are on the rise (Read our article on exploit kits). Nearly two thirds of all exploit kits now deliver ransomware to your computer (Jumping from 17% to 61%). That means proper web browsing practices are more important than ever.
Phoning It In: Android Ransomware
Got an Android phone? Over the last 12 months, Kapersky reports Android ransomware has experienced a 4x jump. This spike has been largely swallowed in the news by the more spectacular IoT DDoS attacks on the U.S. and Liberian internet, performed by the Mirai botnet.
Make Sure You Have A Strong Backup Strategy
The only surefire defense against ransomware infection is having a strong backup strategy already in place. We’ve written an article on exactly what that involves, and it’s well worth a read. As always, we highly recommend implementing a 3-2-1 backup strategy.
If you don’t have backup and disaster recovery software already, we suggest using BackupAssist. Download the free 30-day trial to get started.