A strange new ransomware strain, GandCrab, is making the rounds – and it’s using social engineering to trick users into downloading it.
GandCrab is being sent out as part of a mass spam campaign to tens of thousands of users per day. Servers hosted by the US are by far the most common target.
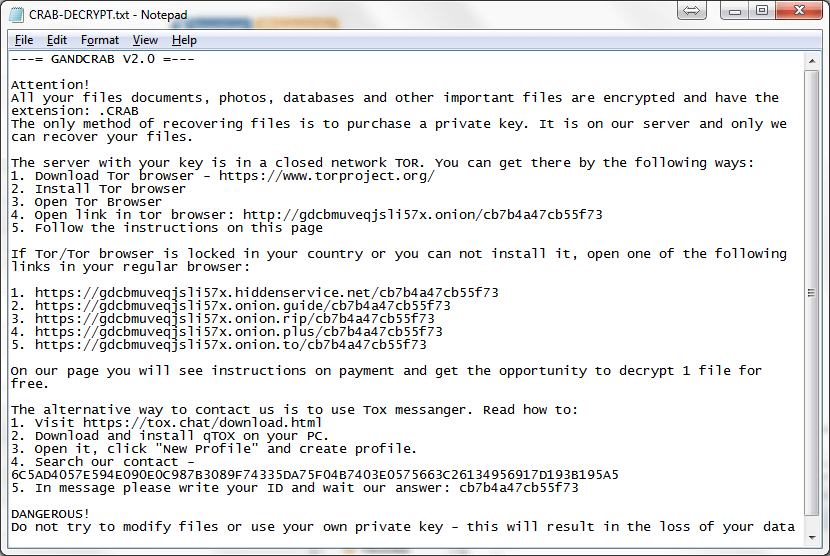
Users with machines infected with GandCrab are being directed to a Tor-only accessible site where they can purchase a decryption key. The ransom is doubled if the payment is not made within a set period of time.
Unusually, the ransom must be made with Dash Cryptocurrency instead of BitCoin. This is likely because Dash is faster to process and harder to track.
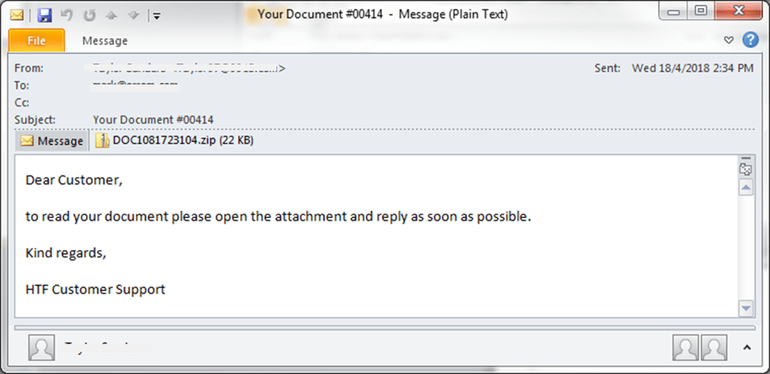
The phishing emails use fairly common social engineering techniques: mentioning payments, tickets, invoices, and orders. They contain a Javascript attachment that, when executed, downloads the GandCrab ransomware from a malicious URL.
When the ransomware activates, it uses an RSA algorithm to encrypt the victim’s files, then adds “.GDCB” and “.CRAB” to their extensions.
The makers of GandCrab are selling their ransomware on a top-tier Rushian hacking forum as Ransomware-as-a-Service, with the creators taking up to 60 per cent of ransom fees paid to their clients. And in exchange, the creators perversely offer step-by-step instructions via the use of a ticketing system.
Even more strangely, the ransomware has terms and conditions. The authors explicitly instruct users not to target Russia, or any other country in the Commonwealth of Independent States of former Soviet republics.
How to Stop GandCrab
Researchers at security company Fortinet have warned those infected with GandCrab not to pay the ransom, because “this does not guarantee any actions from the threat actors.”
This falls in line with recent figures that show only a quarter of those who pay a ransom actually get their files decrypted. The experts advised the best response is to “always have a backup stored in an isolated network environment in order to successfully recover a compromised system,” as well as exercising “good cyber hygiene and safe practices.”
If you’re running a Windows-based server, BackupAssist is a backup and disaster recovery solution that comes with a cutting-edge ransomware defense tool (CryptoSafeGuard). Not only does this combine the best aspects of ransomware defense, it also compliments other solutions such as anti-malware software and firewalls.





