The Definitive Ransomware Protection Guide for Business in 2020.
Ransomware is a huge threat to businesses. The best time to protect yourself from ransomware is before it strikes. Cyber-resilience requires the right ransomware protection to save you from the panic and stress of unplanned downtime and potentially hundreds of thousands of dollars in ransom payments.
Preparation is essential – with the reward of resilience: meaning you can prevent many attacks, and still survive and recover from any attack that slips through the defenses.
In this comprehensive guide, we include specific steps that are often overlooked, show some fascinating real life examples and leave you with a clear understanding of ransomware and how to implement the best ransomware protection – at both a technical and a human-process level.
- Read on and avoid the panic and crisis that often characterize ransomware attacks
Table of Contents
1.0. Know your enemy – understanding what is ransomware and how it works
What is ransomware?
Ransomware is malicious software that “locks you out” of your own data, by encrypting it with a secret key, and then demanding payment for that key so you can decrypt and access your data again.
Many strains of ransomware force victims to take action by incorporating an expiration date into the ransom demand: if the ransom is not paid by a certain date, the decryption key will be destroyed and all ransomed data will be inaccessible forever.
Is ransomware the same as malware?
Where does ransomware come from?
Ransomware originates from cyber-criminals, which can range from “lone-wolf” individuals all the way to well organized consortiums. Such criminals preserve their anonymity and conceal their activities by using tools such as TOR and cryptocurrencies, to the point where it is almost impossible for a regular computer user to know where the criminal is located.
How can ransomware get onto my network or computer?
Broadly speaking, three of the most common ways this can happen are:
1. Self-propagated infection – much like a virus, some strains of ransomware can automatically probe adjacent computers on a network, and “jump” from one host to another, spreading automatically by exploiting certain characteristics and services of a computer’s operating system or application software.
2. Manual infection – involving hackers who can break into systems (via a variety of methods, such as weak passwords, vulnerabilities in protocols such as RDP, or zero-day exploits) and then manually install ransomware in order to monetize their break-in.
3. “Hapless user” infection – where users unknowingly infect themselves by clicking on links in spam or phishing emails, plugging in USB devices, or visiting websites that have been sabotaged.
We describe this in more detail later in the article.
How does ransomware affect your computer systems?
Two common things that ransomware can do to your system is:
1. To prevent it from booting. The Petya (2016) strain attacked the Master Boot Record (MBR) of machines to hijack the computer and demand ransom from the user.
2. To allow booting, but otherwise deny access to data. Here, ransomware will look for data that it thinks has value, like documents and databases, and encrypts that data so that you can no longer use or view it.
What happens when you are infected?
Most ransomware displays an onscreen warning to inform you that your data’s been encrypted. It will also explain how to pay the ransom and that you’ll get a digital key to decrypt your data when the ransom’s paid. Some ransomware will prevent your computer from even starting unless you pay the ransom.
How common is ransomware?
Ransomware is far more common than most people think and reported infections are increasing year on year. According to the McAfee Labs Threat Report (August 2019), the number of Ransomware reports worldwide during first quarter of 2019 was 1.3 million. This was more than double the 600,000 infections reported in the previous quarter at the end of 2018.
Can ransomware infect my backups?
Unfortunately yes. There are a number of ways that ransomware can interfere with backups and render them useless – such as corrupting the backup files from externally, or corrupting the backed up data internally. A good ransomware protection strategy must factor in how ransomware infect your backups.
Can I reuse a previously infected machine?
Due to the risk of reinfection, we recommend against this. The safest method of recovery is to recover from backup to new hardware. This will minimize the chance of reinfection.
Using the existing machine with new hard drives is not the best solution. As we explain in Chapter 3 of this article, ransomware often installs backdoors, which can make it extremely difficult to remove. Backdoors can include modifying the computer’s UEFI Firmware, which can result in reinfection even if the hard disk is completely wiped.
And we absolutely do not recommend continuing to use an infected Operating System. While it might be tempting to use a malware removal tool to clean a machine as the fastest way to get running again, it raises a number of risks such as reinfection, or spreading the infection to adjacent networked machines. If it is absolutely necessary to reuse the infected OS, it should only be a temporary stop-gap solution used in isolation (disconnected from the network) while a proper recovery to new hardware is being performed.
What is the best form of ransomware protection?
As we discuss later, there are both preventative and remedial forms of ransomware protection. For all the reasons outlined later in this article, if you only use one form of protection, we recommend multiple air-gapped backups, as the only fully reliable solution.
For home-users, this can be as simple as manually copying your data to a removable USB drive that you disconnect from your computer. An even better solution is to burn your data to a write-once medium, like Blu-ray disk (albeit limited in storage capacity).
For businesses, the requirements are generally much higher – including restoring servers and mission-critical systems such as Active Directory, email and databases. These backups are generally done by business-grade backup software products, preferably containing active defenses against ransomware that can alert you to data corruption due to ransomware and preserve the integrity of the backup.
2.0. Staying a step ahead - how ransomware gets into your network
This section will leave you with an understanding of what vulnerabilities your business may have, and how an infection can exploit them. This understanding is essential in order to protect your organization against ransomware.
Anatomy of a network breach - how ransomware gets in
The reason why ransomware is so pervasive is because there are many ways it can spread.
Ransomware can get into your network via exploited network vulnerabilities, removable media, remote access tools like RDP, malicious websites and email attachments. Once the ransomware installs on one computer, it can spread around the network installing itself on every device it finds.
This graphic shows the 3 common ways ransomware uses to spread: internet connections, email attachments and infected removable drives. Once it’s on a machine in your network, ransomware can detect all the workstations, servers, laptops and other local networks and spread to them as well.
5 ways ransomware can spread onto your computers
The internet threat
Example: Summer of discontent
To help users work remotely, a company enables remote protocols so users can log into their work computers from their home PCs. A hacker figures out company usernames using an employee email address list, and runs a program to brute force the passwords. 2 days later the password summeR76 works for one of the employee’s PCs, and the hacker installs ransomware, which spreads. Job done!
The attached device threat
Jane uses a USB thumb drive to back up her work laptop. She loses the USB, and gets another one from a drawer at home. At some time in the past the USB was infected with ransomware. She plugs the USB into the laptop, then securely connects to her company network using a trusted laptop, and the USB deploys its ransomware to the company file server. It then spreads, infecting the whole company.
Malicious websites
Example: The doppelgangers portal
A new employee’s told to use a web portal to log their timesheet. They don’t have the site saved so they Google it and select the site name. But the site they selected is .co.rs instead of .co.au. They’re on a malicious site that looks legitimate. They click a link and quickly select okay to a message but nothing happens, so they leave the site and move on to something else. Like most staff, the employee goes home early that day, as there’s something wrong with all the company computers.
Malvertising
Kim recently made a purchase online with a reputable company. After making the purchase, the company’s online advertisements start showing up in her social media. One add prompts her to consider another purchase but she changes her mind. Unfortunately, that’s not the end of it. Hackers have injected malware into the company’s advertisements and Kim and thousands of others notice the computers they used to view the advertisement at work and at home, now have a new flashing message – this time its ransomware.
The email threat
We saved the best until last.
Ransomware can be spread using emails with attachments. Although PDFs and office documents are a lot more secure than they used to be, file compression formats like WinRAR can be used to deliver ransomware, especially if the mail server does not provide adequate mail filtering. The email may sound like a legitimate communication, but once the attachment is opened, it will quietly begin encrypting your data and spreading from one machine to the next.
Although this is one of the oldest forms of ransomware propagation, the McAfee Advanced Threat Research team’s August 2019 report shows that user execution attachments are still used, and threat actors often survey large organizations before sending the emails due to the lucrative returns.
Dave in HR receives an email titled ‘Job application’ with a PDF attached. The email makes sense and Dave opens it to find a poorly written resume for a generic job. He closes the PDF, not knowing that it ran a macro and installed ransomware. Ten minutes later the ransomware has encrypted Dave’s PC and spread to all company PCs and servers. The company is now unable to function or access critical data.
Honorable mention - 0-day exploits
This is the reason why ransomware can never be fully eradicated. It is a special kind of nasty that can apply to any of the previous examples. It can exploit even the most secure systems because the vulnerability the ransomware uses may not yet be known (day 0), so patched and updated machines can still be compromised.
3.0. An unsavory meal – what Ransomware serves up once it’s on your computer
Ransomware starter #1: install backdoors
Ransomware can be clever – trying to get a solid foothold into your computer. Once installed, it can open backdoors in your systems and exploit them later. Examples of these backdoors include:
- Embedding itself into the computer’s BIOS or UEFI firmware, so it can “spring back to life” even if the hard drive is wiped and the operating system is reinstalled.
- Phoning home to the cyber criminals and opening a “shell”, which allows the criminal to directly access and control the machine without you knowing.
It can also do something called privilege elevation, whereby system or user accounts the ransomware may use are given more access. These changes can be used to help the infection spread to secure areas, and open more back doors into your network.
Ransomware starter #2: propagation
Once on a computer, ransomware can locate and spread to any location you can access from your desktop. In fact, with the creation of backdoors, it can probably spread to more locations than you think. And this will happen quickly and often unnoticed, while it’s encrypting your machine.
It is common that in a networked environment, ransomware will spread by scanning for other machines on the network, and then exploiting vulnerabilities in software or lax security configurations to install itself on other machines.
Ransomware main course: encrypt and lock you out of your data
Now the destruction begins. Ransomware’s main purpose is to search for your files and encrypt them, one by one. Unfortunately for us, computer processors and storage drives are so fast nowadays, the encryption can happen rapidly. Encryption expert, Linus Chang, says that on common desktops, “data can be encrypted at rates upwards of 300GB per hour. Most people can be locked out of all their data in just a few hours.”
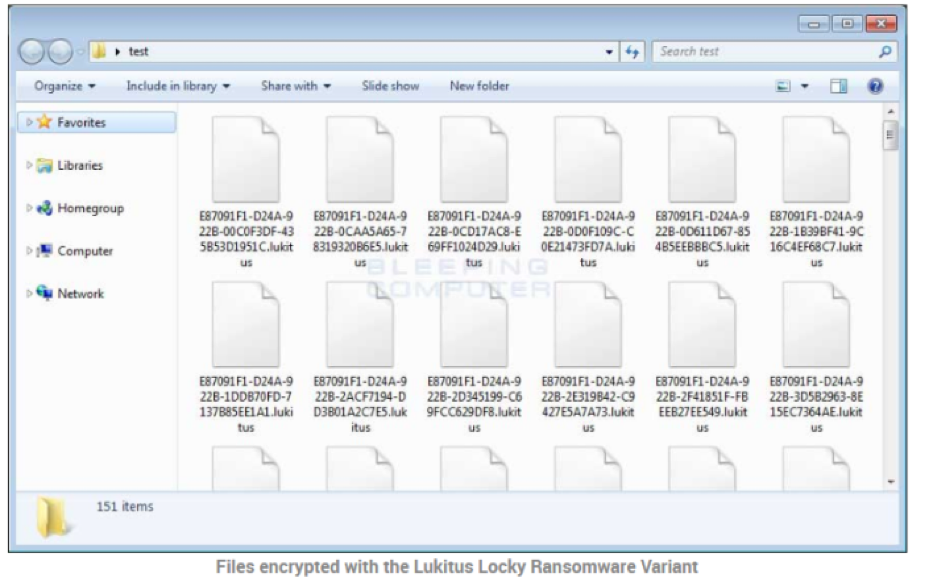
Ransomware will stay hidden and operate in the background locating data it thinks is valuable. For example, everything in My documents, in a folder called photos, all Microsoft Office documents, and files that look like databases. Once encrypted, the files will often appear as files with no application association and if you open them they show gibberish.
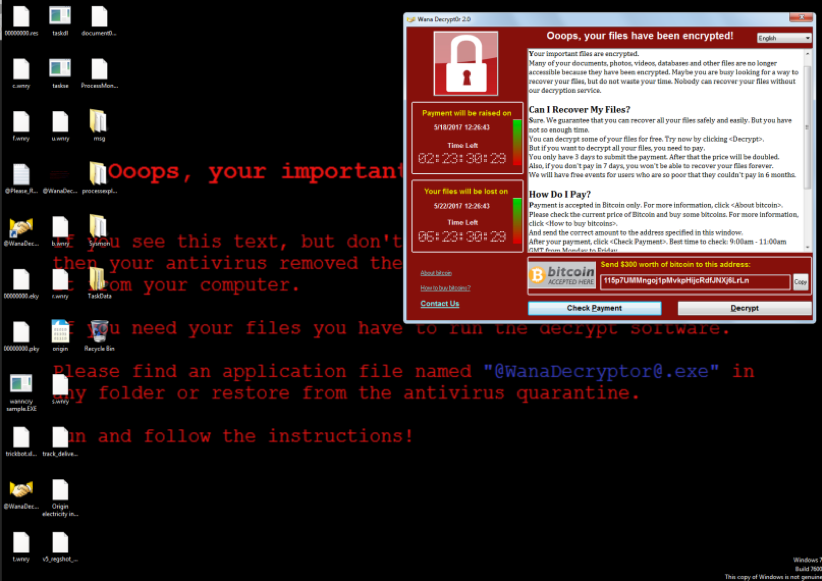
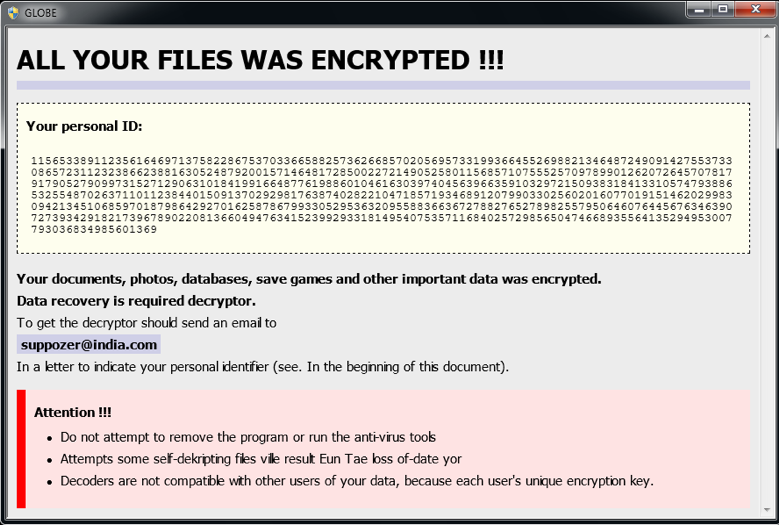
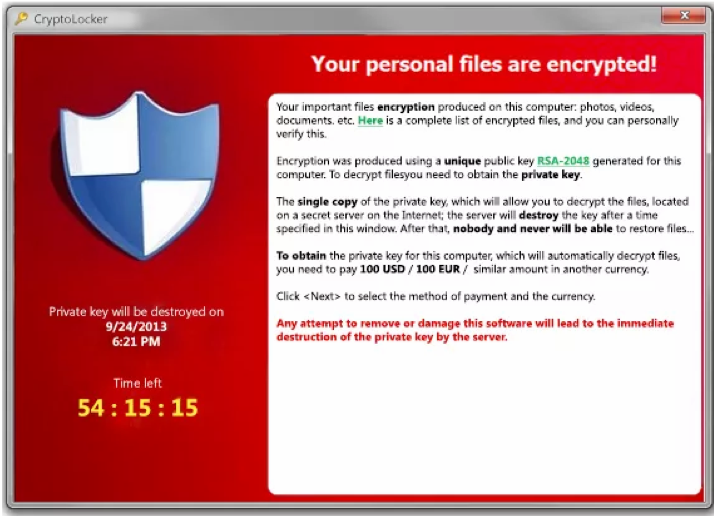
And now you get the check: the demand for ransom
2 examples of ransomware notifications
A ransomware notification will usually:
4.0. The business model - how ransomware makes money and how bitcoin is involved
$ How much is a typical ransom?
Ransoms range from a few hundred dollars to over a million, and average in the thousands. Ransoms have been increasing each year and almost doubled in 2019 to an estimated $12,000.
In 2016, the estimated total cost in the US reached the billion-dollar threshold and by 2018 the global cost of ransomware reached an estimated 8 billion a year.
Over time, cyber criminals have also improved their strategy, focusing on “soft target” organizations who are more likely to pay higher amounts of ransom because of the higher cost of business disruption.
$ What are the additional costs of an attack?
2019 has seen many attacks on public institutions and has a high success rate with counties and schools
demanded in ransom
$ Does paying a ransom fix the problem?
This is a complex question with both immediate and global implications.
Will you get your data back? Most ransomware payments result on the delivery of a decryption key, but about 5% of paid ransoms are not sent a decryption key. But even if your data is decrypted, your network may still be compromised by backdoors and malware. This can lead to repeat victims – users who show they are willing to pay and are targeted again by ransomware.
The lesson here is that if you pay, it may not be the end of it. You could be targeted again and, as explained in the backdoor section, all impacted servers and machines will still need to be rebuilt.
On a global level, many law enforcement agencies recommend against paying the ransom on the basis that it only encourages the cyber criminals. However, for organizations that failed to prepare and institute adequate ransomware protection, this viewpoint is of little benefit.
$ How do you avoid paying a ransom?
This process itself can be a problem because it takes time (often over a week) for an account and wallet to be verified by the exchange, and ransoms often have a limited window of time to make the payment.
$ How do you avoid pay a ransom?
There are only two ways to avoid paying the ransom:
- Accept that you have lost your data, or
- Recover your data from a backup
If you prepared in advance, putting in place robust ransomware protection with the right backup, then the recovery should be both predictable and a matter of following a well-defined process.
Before we continue…
Achieving resilience through the right ransomware protection is attainable for every business…
But little mistakes and oversights can undermine the effectiveness of any backup and recovery plan.
5.0. Staying safe and resilient to ransomware
The 10 building blocks of a ransomware resilient business
Can every business be cyber-resilient by putting in the correct ransomware protections? Yes.
But firstly, it’s important to understand that there is no silver bullet to fight ransomware. It’s impossible to guarantee that you’ll be protected against every attack in the future, because:
- Users will always make mistakes
- Machines are never infallible - vulnerabilities and zero-days will always exist
However, if you follow these 10 key steps to ransomware resilience, you’ll safeguard your organization and its future by taking positive and effective steps towards both prevention and remediation.
Given that prevention is never 100% effective, we always recommend combining it with remediation as part of a holistic cyber-resilience strategy.
PREVENTION - How to repel ransomware
ACTION : check that the antivirus on all servers and desktops is updating correctly.
Set up email filtering on your mail server. Email filters check for spam, emails from suspicious sources, known malware and ransomware, and can also check emails with attachments.
ACTION : check that your email filtering is configured to protect you from ransomware. For example criteria that checks emails addressed to people in your domain that don’t exist.
ACTION : Configure your web browsers to block Flash and Java if those features are not needed, and review any Microsoft Office macros that access the internet.
ACTION : Check your user password requirements and ensure all RDP passwords are strong.
ACTION : Check that administration privileges have only been given to users and processes that need them, and that they are only used for tasks that need those privileges.
ACTION : Develop a suspicious email checklist and distribute it to all staff
This email checklist could include the following:
- Does an email’s wording sound vague?
- Does an email’s address look correct for who the email purports to be from?
- Does an email’s address have modified spelling to make it look like a trusted source?
- Are there any spelling errors in the main part of the email?
- Is there a sense of urgency?
- Do you recognize the attachment’s file extension?
If the answer to any of these is yes, then there is every reason to be concerned and your IT support should be informed. If you have the option, call the sender to verify the email.
REMEDIATION - How to recover from a ransomware attack
The mistake many people make is setting up their backup system once, and letting it run for months or years without ever testing a recovery. The problem is that things can change over time:
- Administrators can add extra hard drives or Network Attached Storage but forget to change their backup configuration to add the new storage devices to the backup
- Backup media – such as hard drives – can become worn out over time and stop working
- Hackers can disable or sabotage the backups ahead of a ransomware attack, to make it impossible to recover.
Monitoring and testing your backup system enables you to detect these and other problems ahead of time.
The difference between a panicked and efficient response can be the existence of a documented response plan. It does not need to be long or detailed, just the steps to go through when an infection is detected. What are the first 4 things you should do? Who should be contacted? How or when do you recover? How do you work out what has happened? All these questions have answers but they need to be thought through and agreed on.
- Look at the section below for guidance.
- Look at online resources for guidance
- Get input from stakeholders and IT staff.
- Test your Ransomware Response Plan by performing the documented tasks
- Get approval across the business
- Distribute the Ransomware Response Plan and train staff in how to use it.
- You cannot be Uncle Scrooge and ransomware resilient at the same time!
- If there's one lesson to learn from history, it's this: INVEST IN DATA PROTECTION
ACTION : Review this list and note any items worth following up for your business
Audit your systems to see if any of them should be upgraded to more secure versions
6.0. Zeroing in on backups – do your backups deliver the right ransomware protection?
In the previous section, recovering from a backup is the only sure way to get your data back without paying the ransom. A solid backup strategy is the cornerstone of any ransomware protection system.
So let’s see if your backup plan is up to scratch – by taking a quiz!
How effective are your backups as a ransomware protection?
I use the right backup type
The right backup type for you will be one that successfully recovers a computer from a backup to a new or reformatted disk. It is possible to recover from a file-based backup - that is, you back up only your files, but not your system. However if you do, you’ll have to rebuild your machine, install the Operating System and all applications, and make any required configuration changes. This might be easy if your organization uses a Standard Operating Environment (SOE), but for SMEs who do not use SOEs, this is going to be troublesome and result in more downtime. If that is the case, we recommend creating full image backups of your systems. An image is a snapshot of the operating system and all data on the disk, and it can be used for a bare-metal recovery.
YES
NO
I use a secure backup destination
If your backups use destinations you can browse to, then ransomware can infect them. The best option is to always use secure backup destinations. These are often called offline or air-gapped destinations. Examples are media that are disconnected after each backup and authenticated cloud destinations that ransomware cannot spread to.
Warning: If you do use a destination that you can browse to, you must have additional backups that ransomware can’t reach. E.g a weekly backup to a cloud destination, but this means your recovery point is a week old. The best option is to always use secure backup destinations.
YES
NO
I know my Recovery Point Objective
When a computer is recovered from backup, it will be recovered to how it was at the time the backup job started. If your mail server is recovered using a 3-day old backup, you will lose 3 days’ worth of emails. Your recovery point objective (RPO) is how long a gap your business can afford to go back in time - and therefore how frequent your image backups to secure destinations should be made.
YES
NO
I test my backups
Unless you have tested your backups, you don’t know if they work. The only way to test your backups is to perform a full bare-metal server recovery, and to test that the recovered server works as intended.
YES
NO
I train my staff
Performing a recovery of a full system is a lot harder than restoring files. Your IT staff need to be familiar with the process. A ransomware attack is not the time to learn as you go.
YES
NO
- If some of the backup are corrupted due to hardware or data transfer issues
- If the replacement drive fails to meet the requirements for a recovery
- That the process of replacing the current physical drive has no unexpected problems
- That the computer’s firmware supports the recovery process
- That you are familiar with any networking and connectivity requirements
7.0. Hitting pause – a quick review of what we’ve covered before looking at how to respond to a ransomware attack
A Business Continuity Plan
This is outside the scope of this document and there are plenty of resources online. The best way to begin is to go through each business function and look at ways it could be performed without computers. It could be using pen and paper, phone apps, relocating to a partner site or just deciding it can’t be done and what that would mean. The main thing is that this is all considered, team by team, function by function, and documented.
A Ransomware Response Plan
This lays out the process to follow when a ransomware infection is detected. The goal is to minimize the impact and work quickly towards a solution. In the next section, we will go through 4 steps to consider when formulating this plan.
A Disaster Recovery Plan
This explains the technical steps to follow when performing bare-metal recoveries of your systems from backups. This is a technical document, but in the section below we’ll go through 5 steps to consider when formulating your plan.
8.0. Ransomware protection resources – key products and tools to help you before, during and after a ransomware attack
Before an attack – ransomware detection and protection solutions
- Detects and stops attempts to remotely execute code in your system.
- Monitors files and network and process activity for signs of malicious behavior.
- Looks for anomalies suspicious executables on your computer.
- Record changes to your data and rolls back those changes to undo encryption.
- Provides intrusion detection for virtualized environments.
- Uses machine learning to detect zero day threats.
- Has real-time communication between the threat detection features.
- Can include an integrated firewall to block persistent threats.
- Record changes to your data and rolls back those changes to undo encryption.
- Uses a file server agent to monitor activity and looks for signs of ransomware.
- Blocks malicious websites and filter emails with malicious attachments.
- Removes unsafe browser extensions.
During an attack – ransomware identification and decryption solutions
Once you identify the ransomware, check if there’s a decryption solution available. Two useful resources, WatchPoint and nomoreransom.org, can help determine if there is a decryptor available for your strain of ransomware. There are also decryptors available from Avast, AVG, Kaspersky and Trend Micro.
Online resources
9.0. Ransomware Response Plan – What to do during a ransomware attack
As someone responsible for fixing the ransomware attack in an operational or IT capacity, the saving grace is that you have a plan, you’ve tested it, and you have backups ready to go. But what should be in your response plan?
In the previous section, we looked at the tools and technical resources that can be used during a ransomware response. In this section, we look at processes and decision points to consider when making a response plan.
For Small and Medium Business
1
-
Cauterize the wound
As soon as ransomware’s detected, all machines should be disconnected from the network to prevent the infection from spreading by pulling out the network cables and turning off the machines. This includes connections to other networks, sites and remote devices. -
Quarantine the backups
A recovery needs uninfected backups, so your backup plan should include backups that aren’t online and therefore safe. Backup destinations like NAS devices and removable drives should also be isolated. Recall offsite backup media so they’re ready to use.
2
3
-
Confirm the infection
Some malware claiming to be ransomware is just an onscreen message claiming to be ransomware and asking for a bitcoin payment. Turn on an infected machine and confirm it’s a real ransomware and that data has been encrypted. -
Understand the ransomware
Review everything known about your strain of ransomware. Learn from those who have faced it, specifically: are there known solutions and does this ransomware present any risks to backups and recoveries. If there is a ransom notice on screen, take a photo -
Know the damage
What has been infected and what may have been infected. Run a quick audit to identify the extent of the infection. See if any machines have not been infected.
- What machines are known to be infected
- What machines showed no sign of an infection but may be infected.
- If you have multiple sites or LANs, was ransomware found in the other locations.
- Were any machines in the company turned off - these may be clean.
Once you know what was infected and have your backups and staff ready, you can recover your machines using their backups. This process should also be documented as part of your Ransomware Response Plan or as a standalone Disaster Recovery Plan.
For best results, these are our recommendations for recovery:
- Recover from backup to new hardware – which minimizes the chance of reinfection. It is highly unlikely that newly purchased hardware will contain ransomware on it.
- If existing hardware must be used, then completely wipe the machine, and either rebuild it from the Operating System up, or perform a bare metal disaster recovery (BMDR). However, we cannot recommend this method because there is still a risk that formatting the machine’s disks won’t fully remove the malware – malware has been known to infect BIOS / UEFI firmware, so it can reinfect the machine.
- We strongly recommend against reusing a previously infected machine and relying on a malware removal tool to clean it. While these tools can be effective, they can never guarantee success.
4
Larger Businesses
Possible steps to add for larger organizations:
- Set up an incident room and rooms in regional hubs to manage the response
- Inform stake holders
- Contact specialized consultants
- Contact specialized consultants
- You don’t know how long the ransomware infection has been on your network. Machines you think are safe may have ransomware installed.
- Machines can be turned on to confirm an infection if they are isolated, but this can allow a partly complete infection to continue encrypting local data.
- You can start machines from external drives using virus detection tools to check for ransomware without the ransomware running, because the computer itself is not started.
- Uninfected machines or LANs provide an opportunity to resume business functions BUT you would need to be very certain they are clean before connecting and using them.
- The only way to be sure you have removed ransomware from your network is to perform a full recovery of all machines. In fact, you should also replace the hard drives first.
10.0. This section explains 5 key disaster recovery steps in a ransomware scenario.
1

CASE STUDY
Being able to recover a domain controller is critical for business operations, as Maersk, the world’s largest shipping conglomerate, found out when it was hit by a cyberattack and all 150 of its domain controllers were wiped. They relied on the servers acting as fallbacks for each other, and the company was only saved when one remaining domain controller was found in the Ghana office, because there had been a power outage at the time of the cyberattack.
Due to the poor network connection, an employee at the Ghana office was flown to Nigeria with the domain controller’s drive, and then another employee flew with it to London – delivering the drive that the whole company needed to start the recovery process and allow 20% of global shipping to resume.
Read the full amazing story.
Ransomware can perform actions that change access permissions, leave back doors and maybe even create spaces in which it can hide – including the BIOS / UEFI Firmware of the infected machines.
For peace of mind, and if feasible, replace all infected machines with new hardware. This minimizes the chance of reinfection.
2
Replace all infected machines
3
The ransomware attack on the city of New Bedford, Massachusetts, is a good reminder that even if you are prepared and take the right steps, recovering from a ransomware attack takes time, money and planning. In this case, the city of New Bedford had followed many best practices with a compartmentalized network and activity monitoring. In July 2019, this monitoring detected signs of malware that led to the IT department shutting down the city’s network, hampering a ransomware infection that was already spreading. This quick response meant only 158 computers were infected out of 3,500. However, to ensure the ransomware was removed, the IT department rebuilt the entire server network, replaced affected computers and recovered all applications from backups.
4
5
Thanks for reading our ransomware guide.
We would be happy to help you explore our solutions and answer any questions this article has raised during a free 15 minute consultation. No strings attached! At the end of the call we will provide you with download links and a 30-day evaluation key so that you can experience firsthand the peace of mind that BackupAssist provides.
Don’t wait, contact us now to request your one-on-one session with one of our Client Success team members.