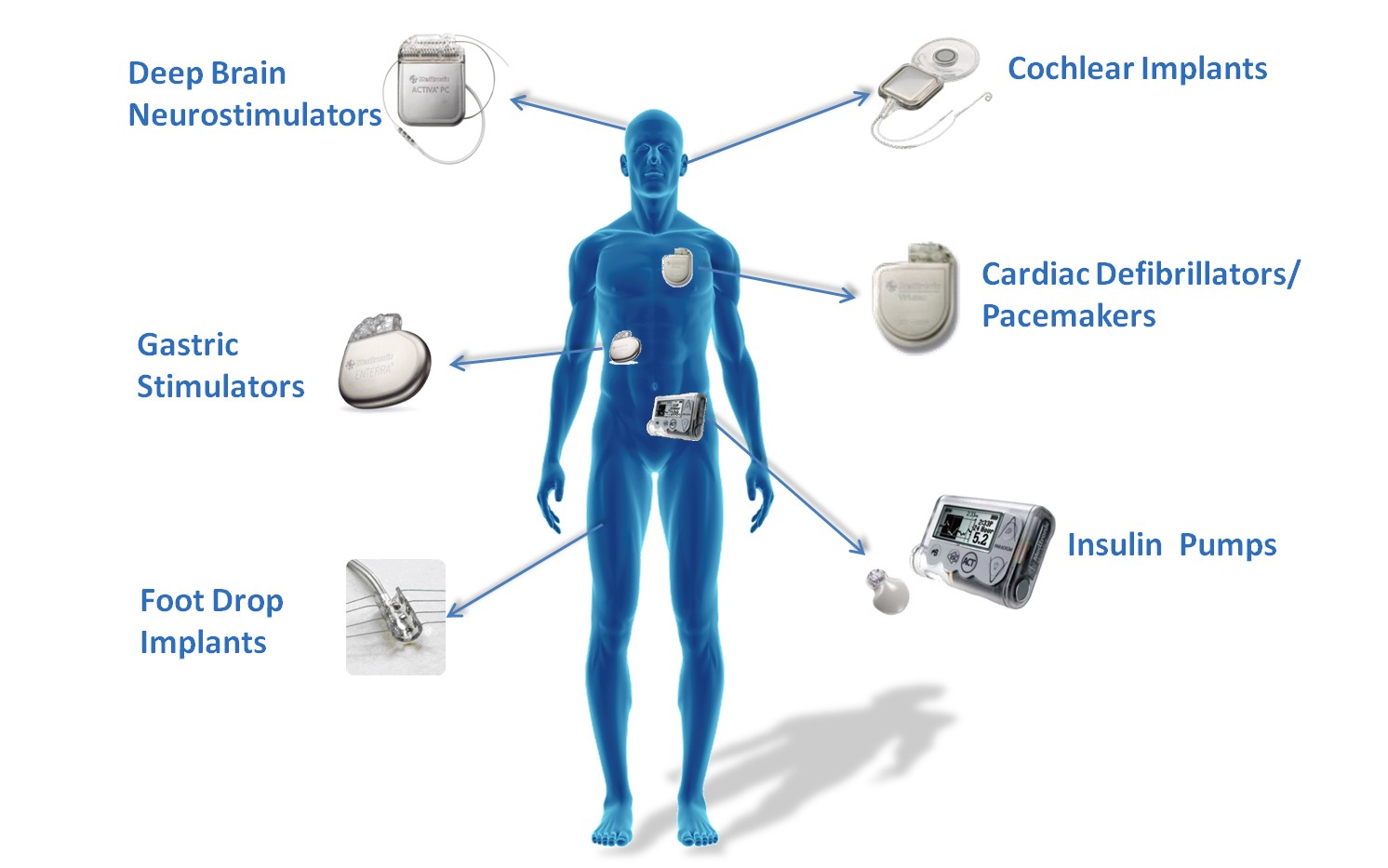
You know you’re living in the future when half a million people are called in for a personal firmware update.
Two weeks ago, the Food and Drug Administration (FDA) recalled 465,000 pacemakers after discovering security flaws that could allow hackers to run batteries down or alter people’s heartbeats.
In May, researchers at a security firm discovered these and many other pacemakers could be intercepted using equipment as cheap as $15, and all bought on eBay.
Since pacemakers are battery-operated devices that are surgically implanted into a patient’s chest to control their heartbeats, the risk to human life was obvious.
“As medical devices become increasingly interconnected via the Internet, hospital networks, other medical devices, and smartphones, there is an increased risk of exploitation of cybersecurity vulnerabilities, some of which could affect how a medical device operates,” the FDA stated in a security advisory.
Is The Risk Real?
Hospitals are already frequent targets of ransomware attack, because hackers know people pay quickly and without question when lives are on the line. The medical industry is also one that has shown high vulnerability to exploits.
Researchers have discovered unencrypted patient data stored on pacemaker programmers: names, phone numbers, medical information, and Social Security numbers. Many pacemakers don’t even have a login name and password, allowing open access to control someone’s heart so long as they’re within range of the device.
While there are no current attacks on people’s pacemakers taking place, there is ample precedent to believe hackers have the motivation, means and lack of moral scruples to do so. Getting ahead of the trend is a smart move.
The devices identified at risk were six types of pacemakers, all made by health-tech firm Abbott’s (formerly St. Jude Medical). These included the Accent, Anthem, Accent MRI, Accent ST, Assurity, and Allure models. All of these models are radio-frequency enabled.
Thankfully, the pacemakers do not need to be removed to be updated – a process that would involve invasive surgery, since pacemaker leads go into the heart. Instead, the firmware update requires a visit to a healthcare provider, and takes approximately three minutes.
After the firmware is updated, any device attempting to communicate with the pacemaker requires authorization to do so. The firmware update is now available, and all pacemakers made after August 28, 2017 have this update pre-loaded into the device.
But Doctors Aren’t Happy With The Added Security
In this case, the cure may cause more trouble than the disease. According to Matthew Green, a computer science assistant professor at John Hopkins, putting security on medical implants could tie the hands of medical staff during an emergency situation.
“If you require doctors to log into a device with a password, you will end up with a post-it note on the device listing the password,” Green said.
This risk doesn’t seem to have daunted the pacemaker manufacturer, who has introduced data encryption and the ability to disable network connectivity features, according to a press release published on August 29.
The debate has wider relevance than pacemakers, as other devices such as insulin pumps have similar security vulnerabilities.
UPDATE: Now it turns out syringe infusion pumps used in acute care settings could be remotely accessed and manipulated by hackers to impact the intended operation of the device, ICS-CERT warned in an advisory issued this week.
These are the devices used for delivering small doses of medication in acute critical care, such as neonatal and pediatric intensive care, and in the operating room.