You’re browsing the web on a trusted website. You click on an regular-looking link. Suddenly, the website changes on you. A splash screen appears. You read it out, a pit forming in your stomach as you see the skull above the text.
‘We have encrypted all of your files. The only way to get your files back is to buy our decryption software. You have 94 hours to pay us, or your files will be permanently destroyed.’
How did this happen? You were just surfing the net—and you weren’t even on a suspicious website! The answer? You’ve been hit by an Exploit Kit.
So, What Exactly Is An Exploit Kit?
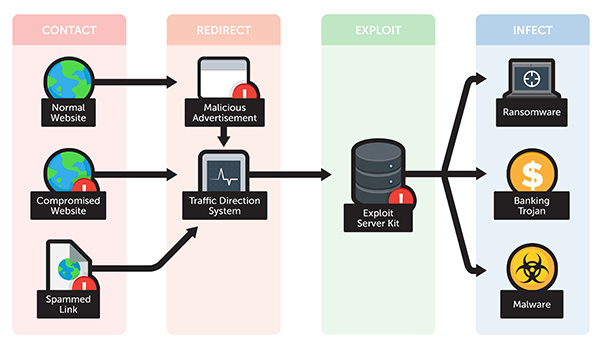
An exploit kit is a hacking toolkit that cybercrims use to take advantage of your old, outdated software. Like a big cat on the Savannah, they watch the herds of traffic going by… then pounce on the weaker members that lag behind.
To use less metaphor, it’s a hacking toolkit that provides several different kinds of trojans, malware, and ransomware, all tailored to ‘exploit’ a vulnerability in your existing software. Typically, they target popular products such as Adobe Flash, Java, and Microsoft Silverlight.
When you access a website, the exploit kit analyzes the software installed on the system/devices used to access it. If any unpatched software is detected, that’s when they attack.
How Normal Websites Hide Exploit Kits
To subject an internet user to scanning with an Exploit Kit, they must be tricked into clicking on a link. This is done through spamming them (forcing them to click it to get rid of pop ups) or social engineering lures.
Once the link is clicked, the user traffic is redirected to the exploit kit, which scans the user. Depending on the prey, it delivers an appropriate payload.
Exploit kits are frequently combined with malvertising—malicious advertisements on legitimate webpages. Since these malware ads are on top-tier news, entertainment and political commentary sites, a user’s guard is down. It preys on the fact many users think bad links only exist on bad websites… and out-of-date software.
Phishing Education and Exploit Kits: Only A Half Fix
Unpatched software is just like an open door to your house. Sure, you could blame the people on the street who would happily come in and loot the place… or you could lock your door. They can only exploit you because there’s a vulnerability to exploit in the first place!
Since any link can lead to an exploit kit, that means phishing can take place via e-mail, social media, advertisements, pop-ups, etc. That’s a lot of bait left out, and all it takes is one click to put your servers in hot water.
Preemptively Defending Your Data
Even if you keep your software completely up to date, the tried and true way to protect your data is to double up on it. Use a 3-2-1 backup strategy to make sure your data is secure. BackupAssist has this sort of scheduling available and several others to protect your data.
And while you’re at it, ask yourself this: is the software you’re using to read this article completely up to date?