So you’re responsible for managing the backup systems and I.T. infrastructure for your company, and Coronavirus has unfortunately razed chaos in your community.
The country declares a lockdown. Your business institutes a work-from-home policy, and no one will be in the office for the next 2 weeks… and that may well extend into 2 months.
What should you do to prepare, so that your business remains cyber-resilient?
In this special report, I’ll go through the challenges and downright problems that I see in relation to keeping I.T. infrastructure cyber-resilient during a lockdown, and then some of my suggested recommendations and solutions.
Table of contents:
- no one is there to swap out the backup disks
- when the cat’s away, the mice will play – hackers, thieves, saboteurs
- slower detection of ransomware events
Your goals and requirements for good cyber-resilience
Recommendations for how to stay cyber-resilient:
- make sure you have an offsite and offline “baseline recovery point” as close as possible to the office lockdown date
- perform automated file backups to the cloud during the shutdown period – to minimize potential data loss
- activate SMS alerts in CryptoSafeGuard to be notified of ransomware events
- power down machines that don’t need to be on
• • •
The problems of a lockdown
The unique circumstances of the current Coronavirus lockdowns presents challenges to cyber-resilience. Let’s explore them now.
Problem 1: no one will swap out the backup disks
This is obvious – for the many small businesses who back up to USB Hard Drive, RDX cartridges or tape, there just won’t be anyone at the office to swap the backup devices out.
So if everyone just packs up and leaves the office, the same backup device will remain connected, and your backups will continuously get overwritten. Therefore, your previously solid backup strategy will break down quickly…
If you are relying on swapping out the backup device to get an offsite and/or offline backup, you’ll need to make alternative arrangements (discussed later) to achieve the same level of cyber-resilience.
Problem 2: when the cat’s away, the mice will play – hackers, thieves, saboteurs
Cyber-resilience involves examining the risks to your I.T. infrastructure, and making sure you can recover in case of emergency. Remember that in the case of an office shutdown, there may be fewer people using your I.T. infrastructure, and therefore any nefarious activities may go undetected for longer.
Here are some of the possible cyber-events that are made easier when there’s nobody physically around to keep track of things.
 | Threat 1: A hacker breaks into your network and installs ransomware (the ‘post-compromise’ ransomware attack) |
 | Threat 2: Thieves break into the premises and steal equipment |
 | Threat 3: Malicious employees perform sabotage while few people are watching |
Add to these are the existing threats such as fire, flood, earthquake, and hurricane.
In my opinion, it is the first threat, hacking, that poses the biggest risk in a COVID-19 lockdown. As more and more people get set up with “work from home” arrangements, more companies will be relying on Remote Desktop and other 3rd party remote access tools. Any small misconfigurations in firewalls, or problems such as weak passwords, can make it easier for hackers to break in.
As with any successful hacking attack, any backups that are online (that is, connected to or accessible from any computer on your network) are vulnerable to being deleted.
Problem 3: slower detection of a ransomware event
Normally, detecting a ransomware event is easy. Staff come into work. They try to log into their PCs, and they see ransom notes all over the place.
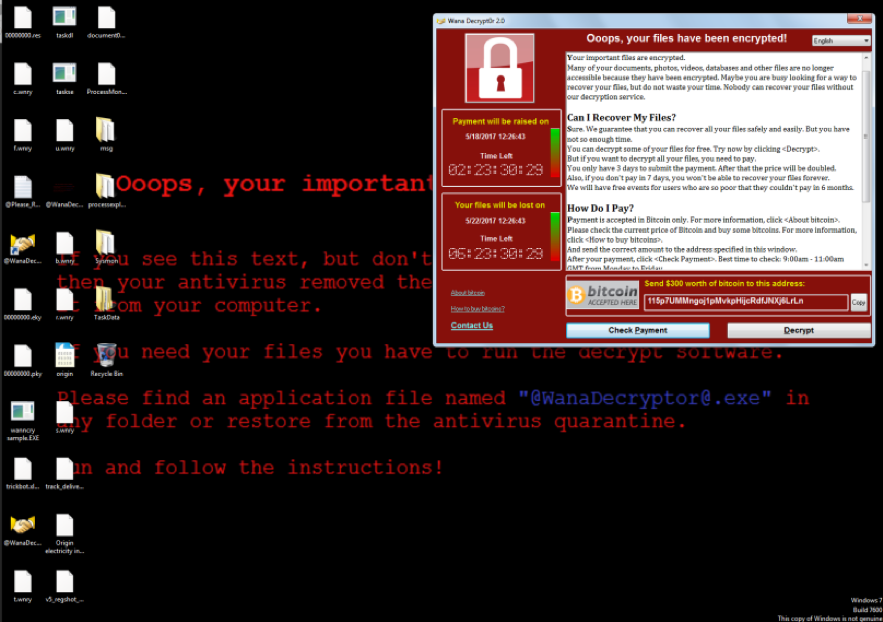
However, in a lockdown situation, it might not be so straightforward. It might be that operations are closed and staff don’t work, so there’s nobody to find the infection. Or in work-from-home situations, the ransomware strain might have disabled remote access, so the ransom message is not visible.
If a ransomware event happens while no one is around, you’ll still need to know about it and take action accordingly.
• • •
Your goals and requirements for good cyber-resilience
The overarching goal in cyber-resilience is to be able to recover your systems in the case of a cyber event.
You can then break down that overall goal into smaller bite-sized goals:
 | Goal 1: To have a valid backup to recover from, and to make sure that backup is secure from hackers, thieves and malicious employees. |
 | Goal 2: To lose as little data as possible. |
 | Goal 3: To recover in the fastest time possible. |
All these three points should make perfect sense. Achieving these goals within the constraints of a COVID-19 lockdown is possible with a little extra preparation.
• • •
Recommendations and solutions
Here are my recommendations on some of the best ways to remain cyber-resilient during times of a COVID-19 office shutdown. You should take these recommendations and use them or adapt them to your own scenarios.
Recommendation 1: make sure you have an offsite and offline “baseline recovery point” as close as possible to the office lockdown date.
For most businesses, this backup should be a full system backup (a system image is fine) that is disconnected from the machine, taken offline and offsite.
Why do a baseline backup?
- It’s important to take this backup offline, because if the office is unattended for weeks, that is a good opportunity for hackers to penetrate the network and destroy the backups. Remember, a hacker cannot sabotage a hard drive or RDX cartridge that is sitting on a shelf! This addresses Problem #2.
- Taking the backup offsite and storing it either in a safe place (like a safety deposit box) or a place that’s inhabited can mitigate against theft or looting. This addresses Problem #2.
- A system image is generally the fastest way to do a full system recovery, just in case you need to. (This satisfies Goals 1 & 3)
How to do your baseline backup
I recommend that this backup is an additional backup to the system you are currently running. Even for larger data sets, an 8TB hard disk retails for around $150, so it is very affordable to take a special, one-off backup for your baseline recovery point. Just configure another system protection job in BackupAssist, and run a manual backup.
This will mean you can recover to the point of the start of the lockdown. But what about work done after the lockdown begins? That’s where my next recommendation comes in.
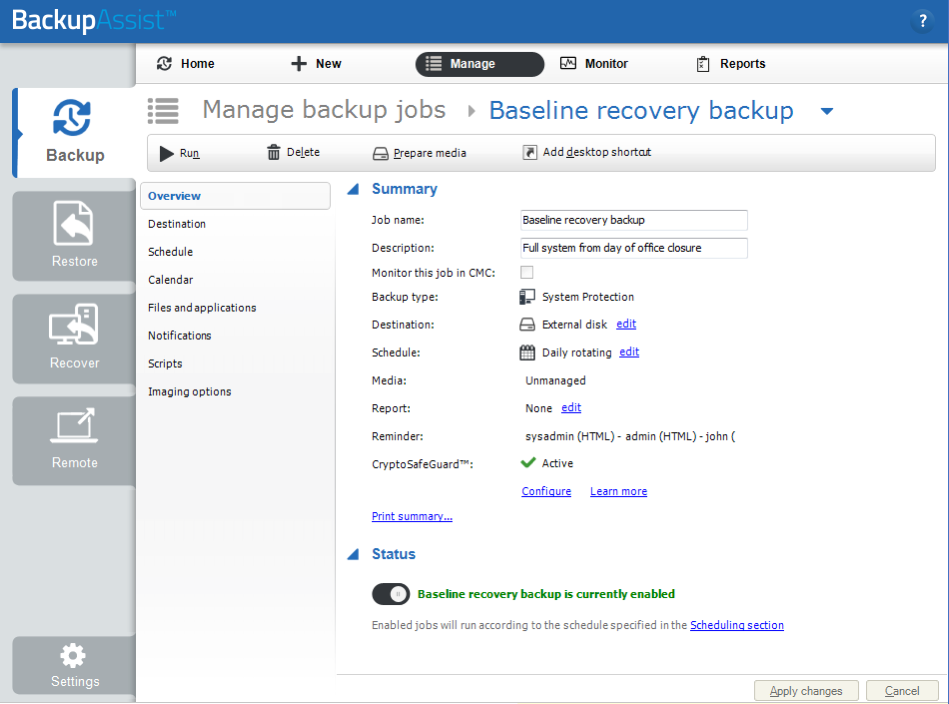
To learn more, see our System Protection documentation.
Recommendation 2: perform automated file backups to the cloud during the shutdown period – to minimize potential data loss.
When there’s nobody to swap out hard disks, you’ll have to rely on fully automated backups. You can think of these as a “top up” backup – your offline system image can be used to recover to the point of the lockdown, and these automated file backups will enable you to incrementally recover to the most recent cloud backup.
Why backups to the cloud?
- Backups to the cloud are automatically offsite. This addresses Problem #2.
- Performing these automated backups will minimize potential data loss. This addresses Goal #2.
- No one is required to make this happen. This addresses Problem #1.
- Unlike other forms of local automated backup (for example, to NAS, or DAS), there is a higher level of resilience in the case of a hacking attempt. Many automated ransomware infection systems will scan and seek out NAS devices. Backups stored in the cloud are safer in that respect (although not entirely hacker-proof, if the hacker manages to steal your cloud account credentials. That’s where 2FA on your cloud account becomes important.)
How to set up backups to the cloud
There are several different options on how to achieve this – which differ depending if you want to back up all your files, or only the most recent files that have changed since your baseline recovery point. This in turn depends on how big your data set is – this will be your call, but I’ll present the different options here.
Option 1: back up all selected files and applications (regardless of how old they are)
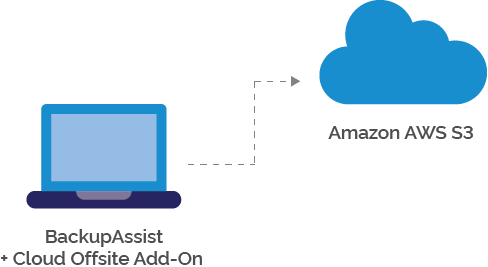
- If you use BackupAssist and are happy to back up to Amazon AWS S3 or Microsoft Azure: set up a cloud backup job. Configure the job by selecting whatever files and folders you want to back up. Note – this requires the BackupAssist Cloud Offsite add-on.
- If you prefer to use other cloud storage options, you can follow these steps to perform a local file backup to local storage, and then use a file sync app to sync them offsite:
 | Firstly, create a new directory to somewhere where you can store a mirror of your files. Then set up a File Protection job in BackupAssist to back up your selected files and applications to that directory. |
 | Second, install your chosen cloud sync application to sync that directory to the cloud. Common choices include the OneDrive app, Google Drive, Dropbox and OwnCloud sync tools. |
 | Finally, if you want a 3rd copy of your files, then use BackupAssist 365 to then download the cloud copy of files back to a local destination. BackupAssist 365 currently supports downloading files from OneDrive, OneDrive for Business and SharePoint. |
To learn more, see our Cloud Backup documentation.
Option 2: back up only the most recent files with the help of robocopy.
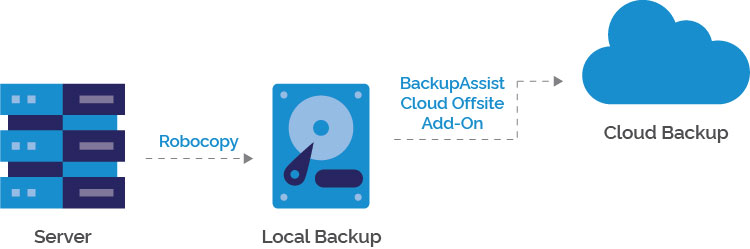
This can be a great option if you have a huge data set, and need to get your cloud backups going FAST. After all, it’s much faster to upload 1GB of data than 500GB. You’ll need to firstly do a local backup of these files, and then you can back up that local backup to the cloud.
This option uses the “robocopy” tool to copy recently changed files to the local backup directory.
- Firstly, you want to get your robocopy script working. I won’t include a full tutorial on robocopy here, but instead cut to the chase – this script will work for most people:
robocopy E:\Work D:\LocalBackup /e /sec /maxage:20200311 /r:3
In this example –
E:\Work is our source directory
D:\LocalBackup is your local backup directory
/s says to copy subdirectories
/maxage:20200311 says back up everything since 11th March 2020. Modify this to your needs.
/r:3 means retry a file up to 3 times, and otherwise skip it. You need this parameter to avoid robocopy trying to retry a million times. - Next, configure the BackupAssist Cloud backup to back up the local backup directory to the cloud. Instructions on how to do this are in our Cloud Backup documentation. We also recommend running the robocopy script as pre-backup script. The instructions for adding a script to BackupAssist are in our Scripts documentation.
When running within BackupAssist, you can also add the /b switch to robocopy – this will copy the files in “backup” mode, which retains NTFS metadata like ACLs.
Note: this requires the Cloud Offsite add-on.
If you aren’t using BackupAssist, you can certainly schedule the scripts and use a cloud sync tool (as mentioned above) to get your files offsite. Then you can use BackupAssist 365 to re-download those files to a different location. However, you may have a problem with silent failures, because the output of the robocopy script and sync results might not be visible to you from the scheduled task.
Recommendation 3 – activate SMS alerts in CryptoSafeGuard
The third recommendation I’ll make is to activate the SMS feature in CryptoSafeGuard. CryptoSafeGuard will automatically scan your backup data set for evidence of files that have been corrupted by ransomware. The SMS feature is very handy, because it means you will be notified if CryptoSafeGuard finds suspicious activity.
Note: This will require a BackupCare subscription.
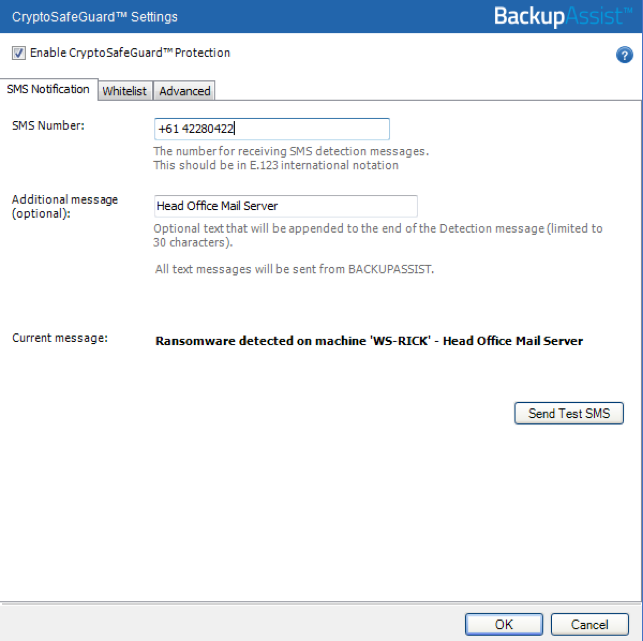
To learn more, see our CryptoSafeGuard documentation.
Recommendation 4 – power down machines that don’t need to be on
This recommendation is a direct mitigation against the threat of hacking (Problem #2).
Remember that every device on your network is a potential entry point for hackers. The only way to reduce the possibility of hacking attack is to reduce your footprint.
Therefore, power down anything that doesn’t need to be accessed during the lockdown. This includes:
- Isolating any routers and switches and taking them offline. Perhaps during a lockdown, only a portion of your subnet needs to be online. Then isolate that subnet, while powering down other subnets.
- Powering down any PCs that won’t be accessed remotely or aren’t needed to support remote access.
- Power down devices like printers – these are known to be potential entry points for hackers.
- Turning off guest wifi access – it’s unnecessary given you won’t be having any guests over.
Let’s all stay safe…
Aside from these cyber preparations that I’ve described above, I’d like to extend my best wishes to our friends and clients all over the world. We have so many clients who are already in lockdown – in places like Italy and South-east Asia. I hope that we will get through this Coronavirus pandemic and that the worst will be over within 3 months.





