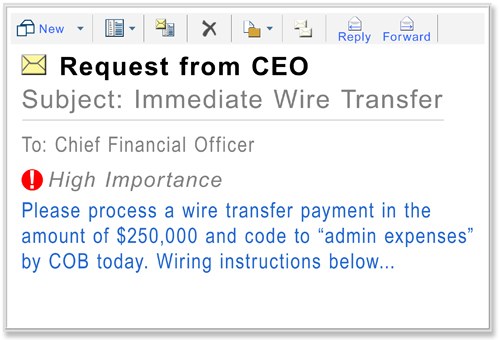
Be really careful when you next get a message from your CEO, even if it’s from a legitimate address. It may not be from who you think it is.
Over the last year and a half, small to large businesses have been hit hard by Business E-mail Compromise (BEC), also known as ‘CEO fraud’.
BEC scams commonly involve targeting specific employees of an organization that appears to be from their CEO, asking for a wire transfer of funds to a nominated recipient. If you’ve got a Chief Financial Officer (CFO), they’re most at risk of this sort of scam.
How Does BEC Happen?
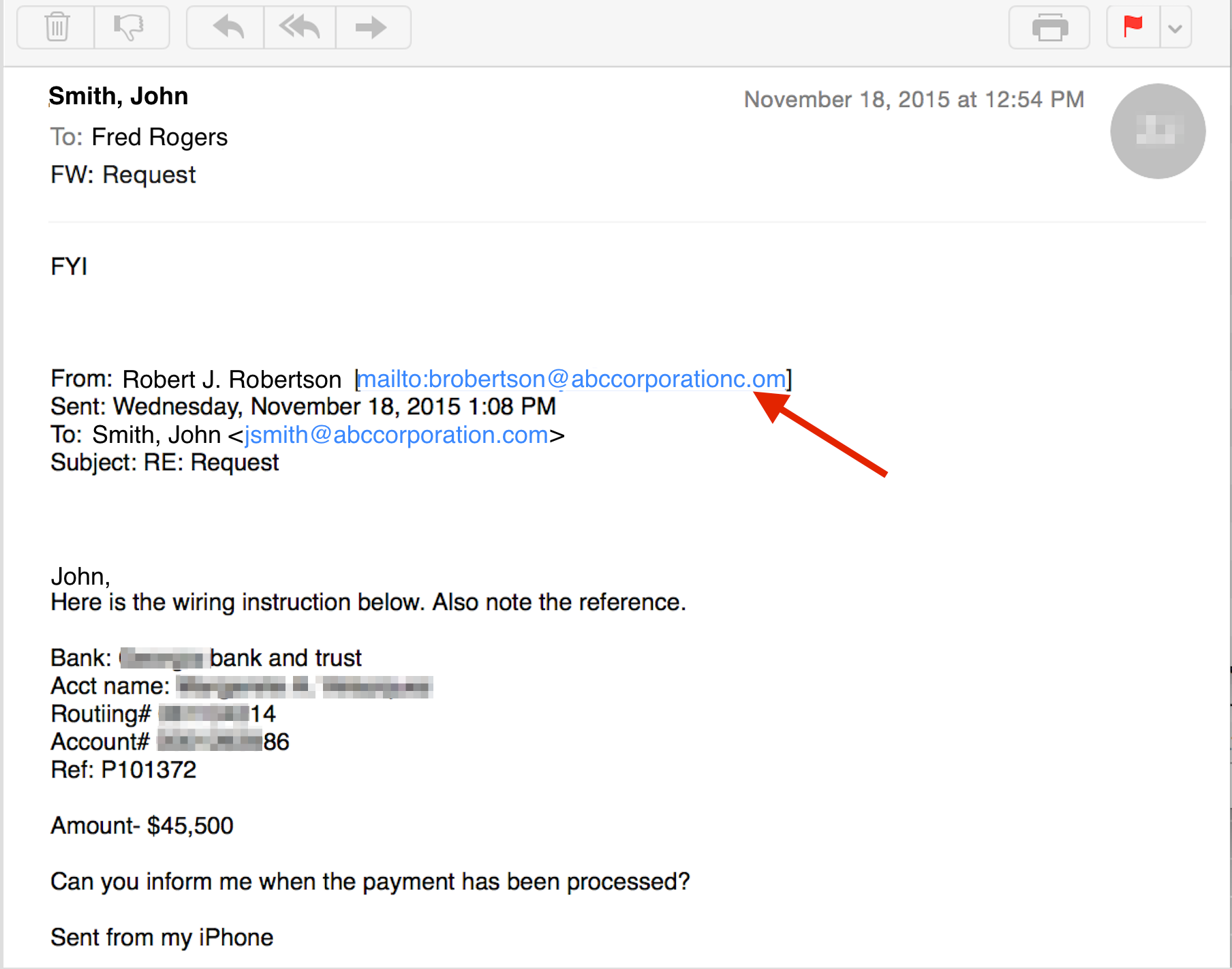
First, hackers compromise the CEO’s e-mail through phishing. If they can’t get your domain name, they’ll use a very similar one.
For example, if your company’s domain name was “example.com”, they might register “examp1e.com” and send it to you. And if you’re a skim reader, you might miss it.
Frequent targets of BEC are organizations that regularly perform wire transfer payment. However, the fraudsters will usually use the method most commonly associated with your business’s normal practices, even if this is check.
If you’re hoping your spam filters will protect you against BEC, think again. It slips right through because thee e-mail is not mass-mailed and targets a specific person. What’s more, it’s usually using a legitimate address. There’s no malware attached; only instructions.
Some individuals reported being a victim of Scareware or Ransomware intrusions immediately before a BEC scam occured.
The FBI reports it has seen a 270% increase in BEC scams since January 2015. It said from October 2013 to February 2016, losses have exceeded USD 2.3 billion.
The Hackers Get To Know You
The real problem with a BEC scam is that the perpetrators get to know your business before they strike. They research the target organization’s relationships, activities, interests, and travel or purchasing plans.
They pull this off by scraping employee email addresses and information from your website. If they’ve got access to your inboxes, they’ll read all your mail before cooking up an e-mail, searching in particular for words to do with invoices, deposits, and your business infrastructure.
Some BEC scammers will even go a step further and look for companies that have seen a change in leadership in the finance section, companies where executives are travelling, or by leading an investor conference call.
On average, the FBI estimates an organization hit with BEC attacks lose between $25,000 and $75,000. Some attacks, however, have cost the victim companies millions or tens of millions of dollars.
What Can I Do To Protect My Business Against BEC Scams?
The best safeguard against a BEC scam is education. Train your staff in noticing the signs that might indicate a scam is taking place.
Here’s what else you can do:
- Be Suspicious: Asking for clarification, forwarding an e-mail to IT, or checking with a colleague is all better than having to admit you transferred tens of thousands of dollars to a fake offshore company.
- Trust Your Instincts: If it feels like something is up, then it probably is.
- Slow Down: BEC scammers often hit your business at the busiest time of the day. There’s a good reason for it; they want you to make a snap decision.
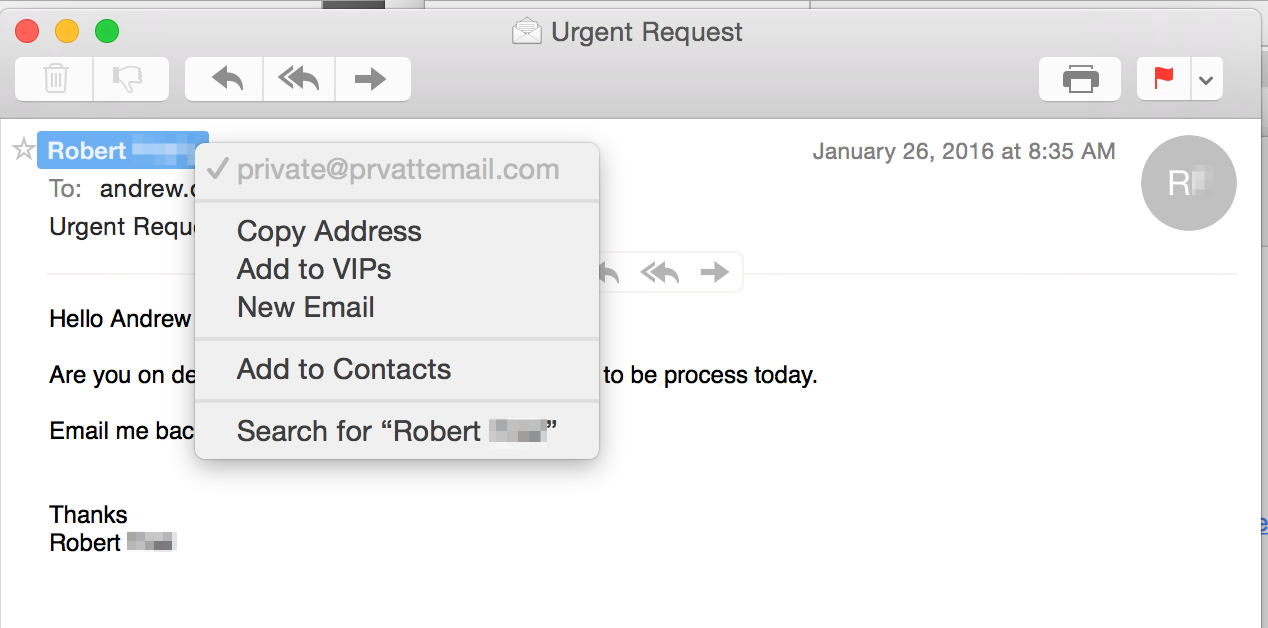
- Check the Domain and Reply-to Fields: Even if it’s often hard to see, the moment you hit ‘Reply’ the real address of the e-mail will show up. This will give a good indication if the e-mail came from a legitimate source. Also check for domain names with typos in it.
- Beware of Personal Accounts: If the e-mail is from a personal account—e.g. “CEOName@gmail.com”—be very suspicious. Not only is it bad practice to use a personal e-mail for work, it’s also a big warning sign a BEC scam is taking place.
- Non-Email Authentication: Make sure when a transaction is taking place, there is a non-email form of authentication. This might be an in person or over the phone request by the CEO so you know they’re really the ones requesting it.
Once you’re secure that everyone knows about the threat of BEC scams, make sure your business is insulated from Ransomware as well—they are often performed alongside each other. Make sure all your business’s data is properly backed up with reliable backup and recovery software like BackupAssist. (You can download the free 30-day trial here)