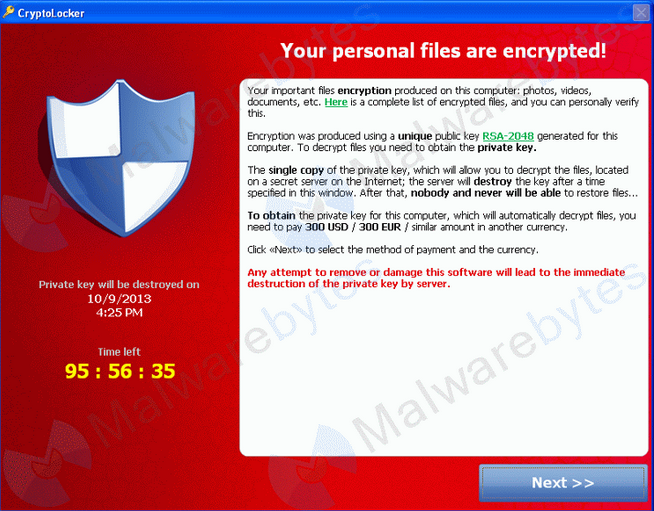
This year saw the arrival of a particularly nasty virus called CryptoLocker. This ransomware will encrypt certain files and then demand a payment to decrypt them. The files cannot be decrypted, other than by paying, so the only safe way to get your data back is by restoring it from a backup.
What makes CryptoLocker of particular concern is that it can also encrypt data on local drives, shared network drives, network file shares, USB drives and (attached) removable hard drives. The infection will even try to delete Windows Shadow Copy backups before encrypting the files, so the shadow copy cannot be used to retrieve your data.
About the infection
- CryptoLocker is a trojan (ransomware) that appeared late in 2013 on Windows computers
- The primary source of infection is a legitimate looking email (e.g. FedEx or UPS tracking notice) with an attachment. The attachment looks like a PDF but contains a ZIP file with an .exe inside it.
- You can also be infected by another infected computer or a malicious website.
- Removing the virus will not decrypt the file, and the files cannot be decrypted by force.
- Data is selected for encryption based on files extensions, incluiding .jpg, .doc, .docx, .psd, .pst.
- A payment of $300 is demanded with a deadline. After the deadline, decryption is offered at a much higher price from an online service run by the CryptoLocker creators.
- Some users report files being decrypted by paying, others report files were not decrypted after they paid.
What this means for backups
There are two critical points about CryptoLocker and your backups
- Any backup on attached or mounted storage, such as a removable drive or a USB device, can be infected and have its files encrypted.
- The encryption cannot be removed or undone without paying, making a restore of the encrypted data from a backup the only guaranteed and safe method of data retrieval.
This means you need to ensure that you have a backup strategy that incorporates a rotation of backups to devices that are retained offline.
How to use backups to protect your data.
Backup rotation
BackupAssist supports and advocates the use of a backup rotation that includes archive backups. Archive backups are defined by your backup schedule. For example, a backup rotation with weekly and monthly backups that are retained offline.
- BackupAssist’s Scheduling step is used to choose the appropriate backup scheme.
- BackupAssist’s Prepare Media step, will electronically label the removable media used.
Offline backups
Backups are designed to protect you from loss of data, including loss due to hardware and site outages. For this reason, offline backups are important because they are disconnected from your network and stored in a secure location. Because offline backups cannot be accessed from the network, they are safe from ransomware infections such as CryptoLocker.
Best practice:
- Use at least three rotating drives / media. If you only have two, you may remove last night’s backup and attach the new device before you realize CryptoLocker has infected your network.
- Have a second tier backup of mission critical files. Easily and cost effective file archiving to thumb drives is a good example of layered data protection.
It is important to remember that viruses and ransomware evolve and their behavior can change.
It is also important to prevent infection with the use of anti-virus software, patches and policies that mitigate the risk of malicious infection.
Important resources
To learn more about protecting your data from CryptoLocker, and what you can do to protect your data, please see these useful resources and articles.
US department of homeland security: https://www.us-cert.gov/ncas/alerts/TA13-309A
Malware bytes: http://blog.malwarebytes.org/intelligence/2013/10/cryptolocker-ransomware-what-you-need-to-know/
Forum repository: http://www.bleepingcomputer.com/forums/t/506924/cryptolocker-hijack-program/page-26#entry3165383
Kreb article: http://krebsonsecurity.com/2013/11/how-to-avoid-cryptolocker-ransomware/